frogy-subdomain-enumeration
Frogy's Subdomain Enumeraton - It's not yet another Subdomain Enumeration tool.
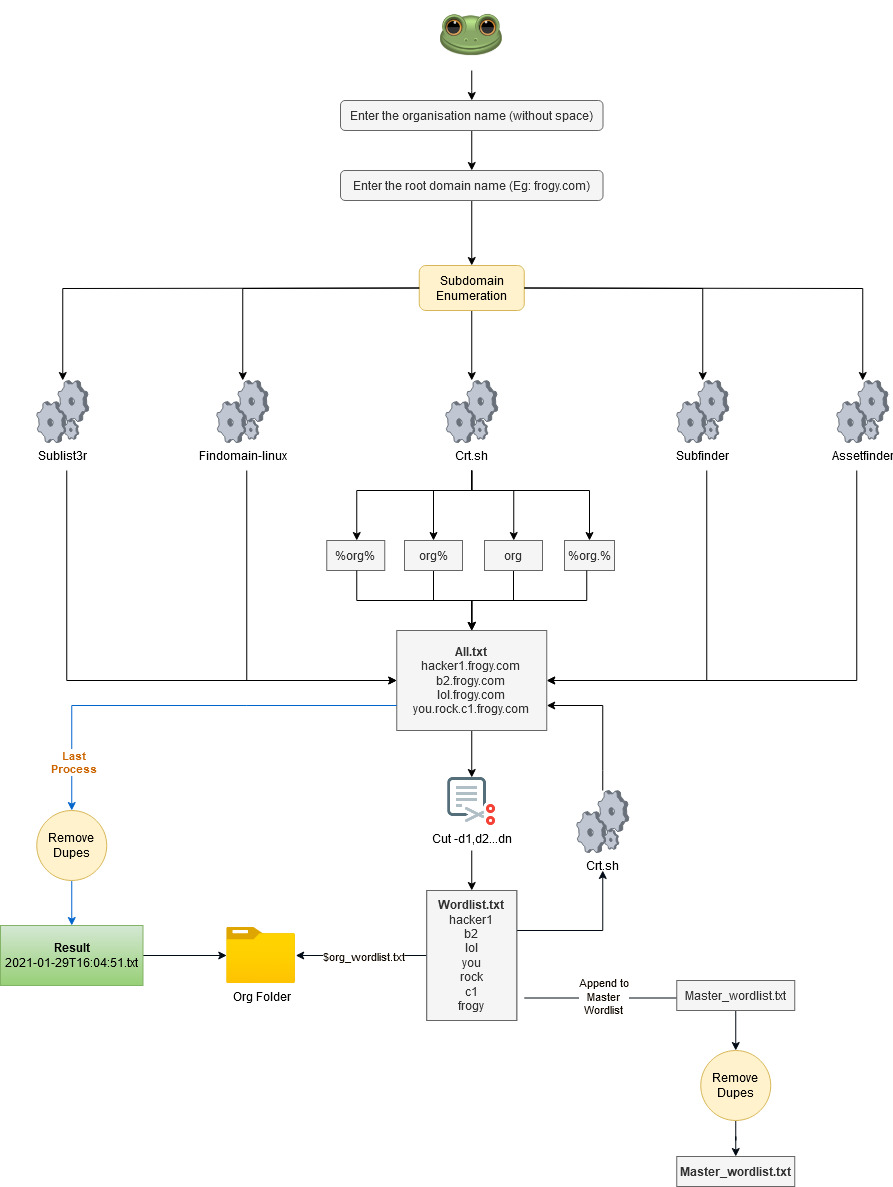
An automation tool that scans sub-domains using multiple tools. Most importantly, it greps all the words from the first, second and N level of subdomains and creates a wordlist. Then uses crt.sh to brute force every single name to identify any hidden subdomains out there.
-
Requirements: Go Language, Python 3.+, jq
-
Tools used - You must need to install these tools to use this script
- SubFinder - Download and put it into the /user/bin folder with executable permission
- Assetfinder - Download and put it into the /user/bin folder with executable permission
- Find-domain - Download and put it into the /user/bin folder with executable permission
- httprobe - Download and put it into the /user/bin folder with executable permission
- anew - Download and put it into the /user/bin folder with executable permission
-
Installation
apt install jq git clone https://github.com/iamthefrogy/frogy-subdomain-enumeration.git && cd frogy-subdomain-enumeration/ && chmod +x frogy.sh -
Usage
./frogy.sh
TODO
- ✅
Efficient folder structure management - Guide on how to find new domains for X organisation on daily basis




